|


Наши программы
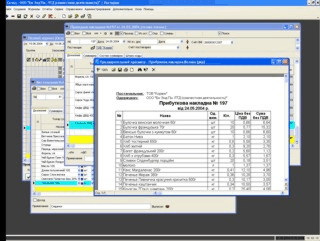
Программа "Корпорация" (ROffice). Клиент-серверная программа для ведения складского и финансового учёта неограниченного количества фирм и складов.
Программа идеально подходит для производственных и торговых фирм, ресторанов, кафе, компьютерных фирм, полиграфических фирм и т.д.
Поддерживается производство, консигнация, реализация, отсрочка платежа, отбраковка товара, возврат товара и многое другое.

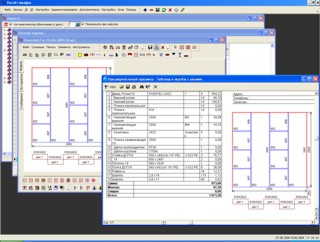
Программа "Расчёт и проектирование шкафов". С помощью инструментария этой программы Вы можете нарисовать шкаф-купе, прихожую, шкаф. Нажать кнопку "Рассчитать" и программа автоматически рассчитает Вам комплектацию. Базу данных комплектующих можно изменять и пополнять. Встроенный редактор скриптов позволит Вам запрограммировать комплектующие и материалы.

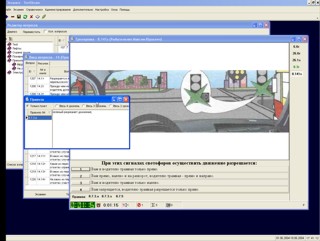
Программа "Экзамен" предназначена для тренировки знаний учашихся и приёма экзаменов. При сдаче экзамена автоматически заносятся результаты в базу данных и формируется ведомость. Возможно вводить вопросы, правила, формировать свои уроки.


Утилита "Буфер обмена". Простенькая утилита, которая показывает содержимое буфера обмена Windows. Этот модуль входит во все наши прикладные проекты.

Утилита "Калькулятор". Самый обычный калькулятор. Этот модуль входит во все наши прикладные проекты.


Утилита "Календарь" . Календарь на 12 месяцев. Этот модуль входит во все наши прикладные проекты. Есть он так же в виде отдельной программы.

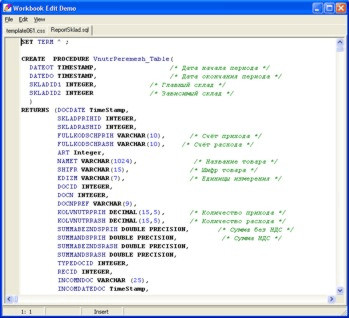
Программа "Редактор скриптов" . Текстовый редактор с подсветкой синтаксиса. Поддерживает все форматы скриптов. 
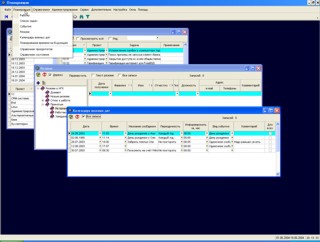
Программа "Планировщик" - программа для контроля своего времени и времени своих подчинённых. Вы можете распределить задачи для каждого подчинённого. Просмотреть выполненные работы, накапрливать базу резюме, а так же указывать важные даты. 
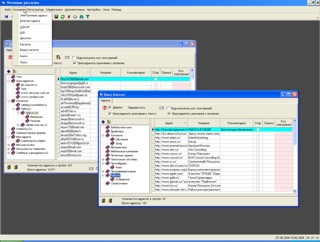
Программа массовой рассылки почты. С помощью этой программы Вы имеете возможность рассылать письма большому количеству абонентов. Можно накапливать базу данных электронных адресов, интернет-адресов, книг, CDROM, дискет, кассет и т.п. 
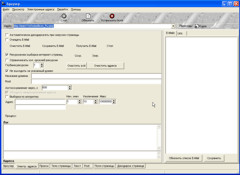
R-броузер - программа для рекурсивного извлечения интернет-адресов из интернтет-страниц. 
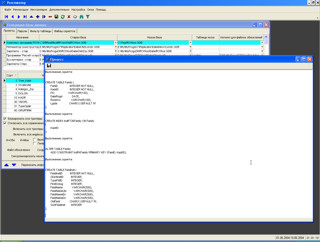
Репликатор - программа предназначена для копирования данных из одной базы данных Interbase (Firebird) в другую. Умеет отключать триггера и ограничения, выполнять скрипты. Поддерживает много-проектность. 
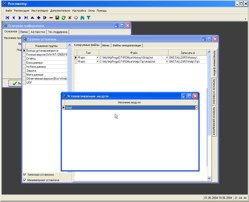
Инсталлятор - программа для создания инсталляционных пакетов. 
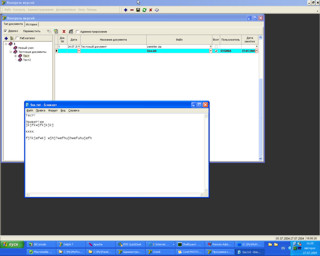
VDoc - клиент-серверная программа для корпоративного хранения файлов, сохранения истории изменения файлов.

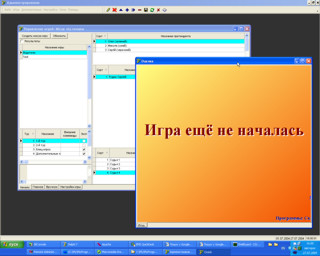
Mesto - Программа для голосования по сети. Применяется при голосовании на телевизионных передачах.

Portal - Программа администрирования порталов нашего производства.


|



